The Cybersecurity Cube
The Cybersecurity Cube (also called the McCumber Cube) is a tool developed by John McCumber, one of the early cybersecurity experts, in order to help manage the protection of networks, domains, and the Internet. The Cybersecurity Cube has three dimensions and looks somewhat like a Rubik’s Cube.
Let's look at each of the dimensions of the cybersecurity cube.
The First Dimension
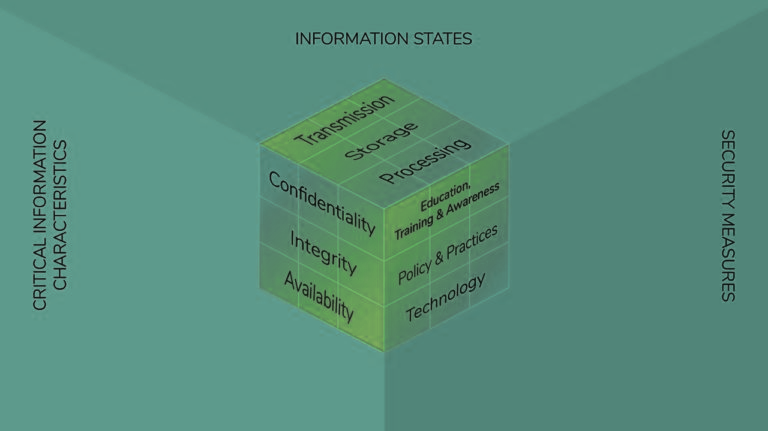
The first dimension of the cube identifies the goals to protect cyberspace. It defines the principles of cybersecurity which is commonly known as the CIA triad.
C - Confidentiality
Data confidentiality means that the information should only be disclosed to authorized people and unauthorized people should be prevented from accessing resources and processes.
I - Integrity
Data integrety refers to the accuracy, consistency and trustworthiness of data. Only the authorized people should be allowed to make changes to the data.
A - Availability
Data availability means that the authorized people should be able to access the data when they need. They should have timely and reliable access to the data and resources.
The Second Dimension
The second dimension of the cube describes the three possible states of the data. They are:
Storage
Data in storage or data at rest refers to the data that is stored in either primary memory or secondary storage in a system.
Transmission
Data in transmission or in transit refers to the data that is travelling across the network from one point to another.
Processing
Data in processing refers to the data on which different operations are being performed to convert it into a desired format.
The Third Dimension
The third dimension of the cube defines the pillars on which we need to base our cybersecurity defenses in order to protect data and infrastructure. It includes the following:
Technology
Technology includes software and hardware-based solutions designed to protect information systems (examples: anti-virus, firewalls, intrusion detection systems, etc.)
Policies and Practices
Policies are formal statements that outline an organization's rules, regulations, and expectations regarding specific areas of operation. Practices are the actions that an organization takes to implement its policies.
Education, Training & Awareness in People
Any system is only as secure as the users of the system. So, ensuring that the users of the systems are aware of their roles and responsibilities regarding the protection of information systems and are capable of following standardsis critical.