The Cyber Kill Chain
The Cyber Kill Chain framework is a part of the Intelligence Driven Defense model developed by Lockheed Martin in 2011 for the identification and prevention of cyber intrusions activity. It explains how attackers move through networks to identify vulnerabilities that they can exploit.
The cyber kill chain is intended to defend against sophisticated cyberattacks, also known as Advanced Persistent Threats (APTs).
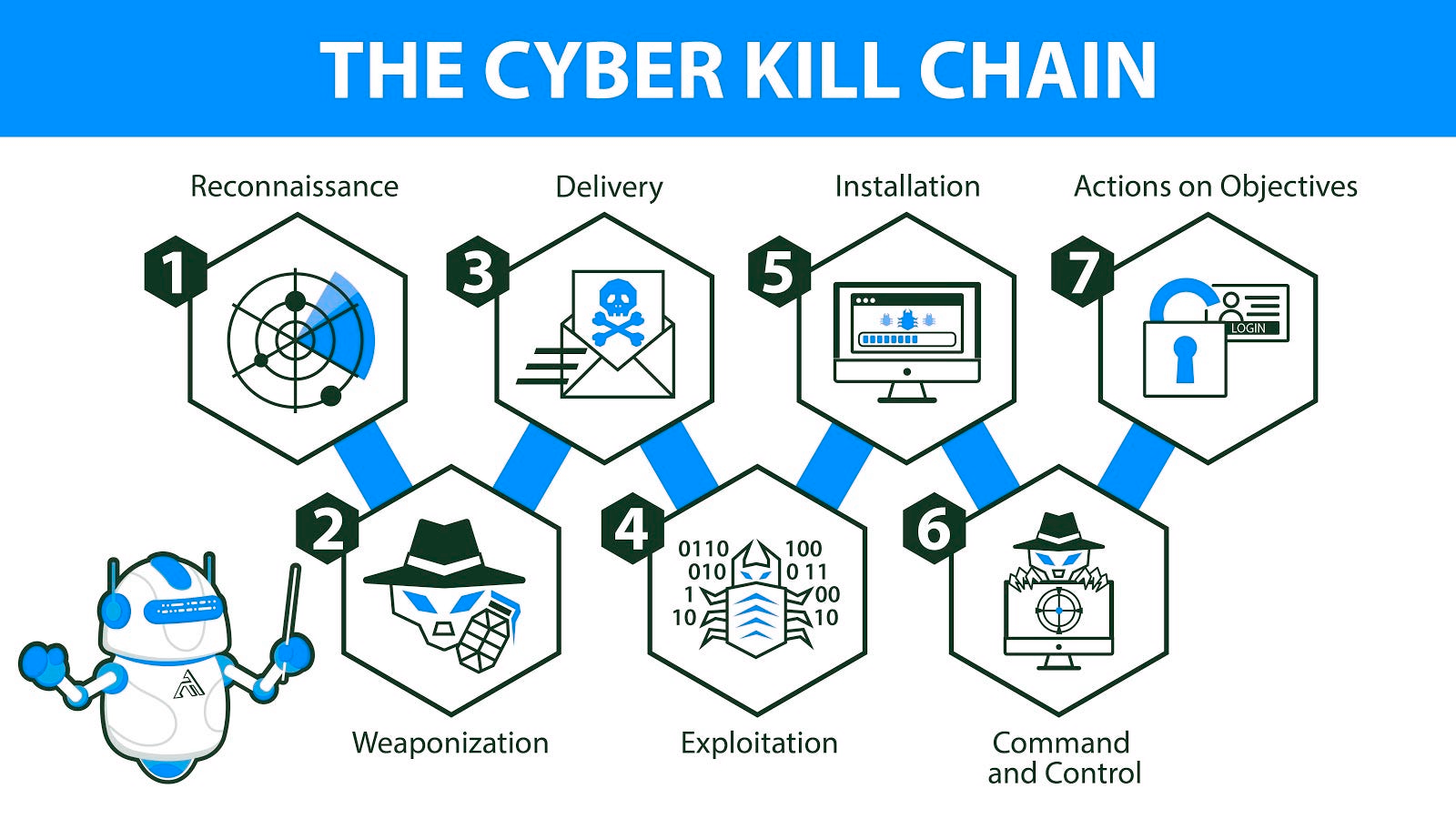
Seven Steps of the Cyber Kill Chain
The Cyber Kill Chain specifies what an attacker must complete to accomplish their goal. The steps in the Cyber Kill Chain are shown in the figure. If the attacker is stopped at any stage, the chain of attack is broken. Breaking the chain means the defender successfully thwarted the threat actor’s intrusion. Threat actors are successful only if they complete Step 7.
1. Reconnaissance
Reconnaissance is the first step in the Cyber Kill Chain where the threat actor performs research, gathers intelligence and selects targets. Any public information may help to determine the what, where and how of the attack to be performed. The more information the attacker is able to gather in this step, the more sophisticated the attack will be and the higher the likelihood of success.
2. Weaponization
Weaponization is the second step where the attacker uses the information gathered during the reconnaissance phase to create an attack vector such as remote access malware, ransomware, virus etc. that can exploit a known vulnerability. There are many attacks that have already been created and tested at large. One problem is that because these attacks are so well known, they are most likely also known by the defenders. It is often more effective to use a zero-day attack to avoid detection methods.
3. Delivery
Delivery is the third step where the weapon for the attack is transmittedd to the target machine using a delivery vector. This may be through a phishing email containing malware attachments, removable USB media or even social meddia interactions. The threat actor will use many different methods to increase the odds of delivering the payload to the target.
4. Exploitation
In the exploitation step, the weapon that has been delivered, is used by the threat actor to break the vulnerability and gain control of the target system. The attacker must use an exploit that gains the effect they desire. This is very important because if the wrong exploit is conducted, obviously the attack will not work, but unintended side effects such as a DoS or multiple system reboots will cause undue attention that could easily inform cybersecurity analysts of the attack and the threat actor’s intentions.
5. Installation
Installation is the step where the attacker installs a back door into the system so that the attacker can use it to gain continuedd access to the target system. The backdoors can be detected by HIPS (Host Intrusion Prevention System) and antimalware scans if they are not effectively hidden.
6. Command and Control
Command and Control (CnC or C2) is the step where the attacker is able to successfully communicate with the remote compromised host and provide commands to it in order to exfiltrate data from the network.
7. Actions on Objectives
Action on Objectives is the final step where the attacker successfully achieves their original objective. This may involve gathering, encrypting and exfiltrating confidential information from the target system. At this point the attacker is deeply rooted in the system and it is extremely difficult to remove the threat actor from the network.
References
- https://skillsforall.com/course/cyber-threat-management
- https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
- https://www.eccouncil.org/cybersecurity-exchange/threat-intelligence/cyber-kill-chain-seven-steps-cyberattack/
- https://www.crowdstrike.com/cybersecurity-101/cyber-kill-chain/